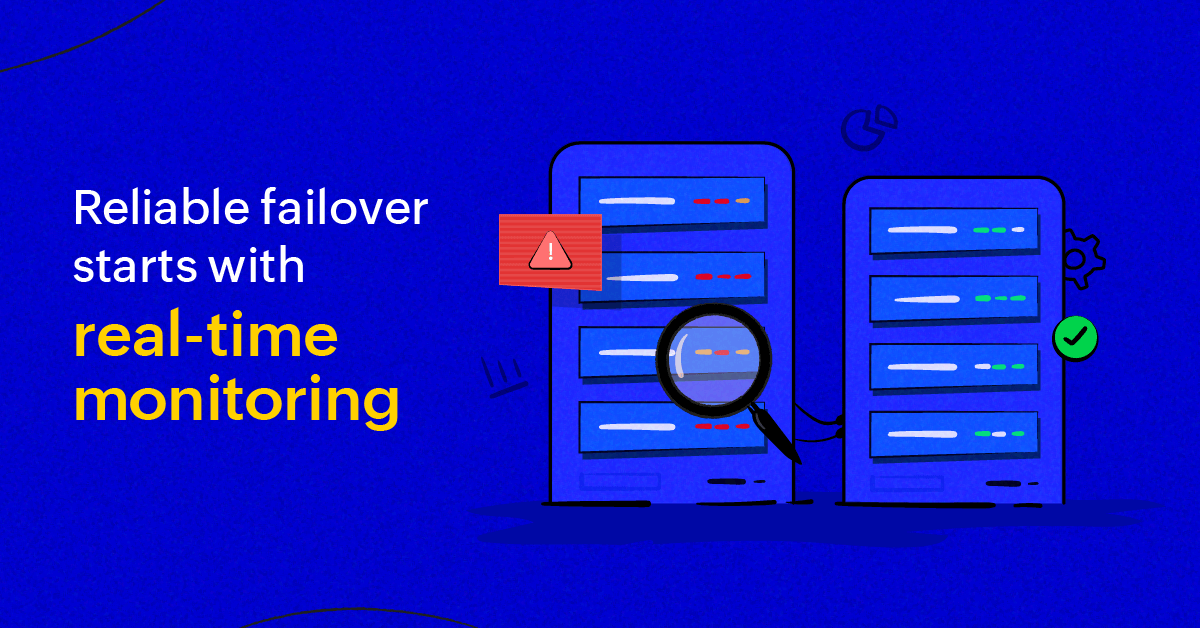
Using Amazon RDS for high availability: How monitoring ensures reliable failover
This blog explores how Amazon RDS achieves high availability, the role of failover, and why proactive monitoring is key for a seamless database experience.
Amazon RDS ensures high availability through Multi-AZ deployments, maintaining a standby replica in a different availability zone. If the primary instance fails, the standby is promo...
Migrating to cloud: Top five reasons
Since the inception of public clouds, a lot of CXOs have considered moving their IT infrastructure to the cloud and many have already done that. If your organization is considering migration to the cloud, learn what drove this mass movement from on-premises servers to the cloud. In this article, we'll explain the major reasons why organiz...
Solving slow startup times in Google Cloud Functions for application developers
Free network monitoring: Full network visibility without the cost
How well-designed automations lead to efficient orchestration in AWS
This blog explores how automation-driven orchestration leads to seamless cloud operations and improves efficiency in AWS environments.
Automation in AWS involves executing tasks without manual intervention, such as scaling Amazon Elastic Compute Cloud (EC2) instances, running Lambda functions, or triggering Amazon CloudWatch alarms. It ...
Kubernetes made simple: A beginner’s guide to managing containers
How APM and synthetic monitoring work together for better performance
Lags are not just an inconvenience—they lead to lost revenue and frustrated users. To prevent this, organizations turn to application performance monitoring (APM) and synthetic monitoring to maintain peak application performance.
In this blog, we will explore why APM and synthetic monitoring work better together and how organizations ca...
Diagnosing ActiveMQ broker performance issues with log analysis
How to leverage AI to enhance network monitoring in retail: A CXO's guide
Diagnosing and resolving the 500 internal server error with Apache and Tomcat logs
To diagnose 500 errors effectively, it’s essential to understand the role of each log type:
Apache access logs record all incoming requests to the web server. They provide information such as the: